Blog > How to Keep Your Business Safe Online
Posted By Create

Did you know that in the UK, 3 in every 10 businesses have experienced a cyber attack in the past year? While many of us are led to believe that cybercriminals are only interested in tackling large scores from big businesses, the reality is that many small businesses are leaving themselves vulnerable to attack and making themselves desirable targets.
On the topic of cyberattacks, it’s easy to think of them as one of those things that will never happen to you (and we sincerely hope it doesn’t). However, with the average attack holding small businesses to ransom for thousands of pounds, protecting both you and your customer’s personal data is one of the biggest responsibilities you have to shoulder as a website owner.
Thankfully, there are measures that you can take to hinder these hackers at every turn. The more difficult you can make it for them to acquire the information they’re searching for, the better your chances of warding off an attack and keeping the data your business holds safe. Read on for what you can get started with today.
Install Security Software
When you bought your laptop or computer, you will have most likely been offered some kind of security package alongside. This software is designed to protect your device against malicious malware attacks and if you haven’t set up protection on your device, this should be one of your top priorities.
What is Malware? Malware is a piece of software that has been created to damage, disrupt or gain access to a computer system. It comes in many different forms such as trojans, viruses or spyware and can be picked up from suspicious websites, email links or other means… Regardless of how it gets onto your computer or why it’s there, you can be sure that it is certain to cause you problems.
This is where security software comes in useful because it can detect, prevent and remove malware (to an extent - depending on what has happened, your device may require professional assistance). The good news is that there are plenty of free versions available online and in most cases, they offer just as much protection as their premium counterparts. You should, by all means, see if any of the additional premium options would be of use to you and your business as everyone’s needs will be slightly different.
As a website owner, malware could potentially compromise your data so it’s important to scan your computer regularly, especially if you think your computer is behaving in an unusual manner and doing things you don’t expect. Being proactive and setting up security software is one of the first and most critical steps to offering you peace of mind that your device is protected.
Strengthen Your Passwords
If you’ve heard it once, you’ve heard it a thousand times. You need strong passwords to properly protect your online profiles. There’s a website called haveibeenpwned.com that has a library of compromised passwords that you can check yours against. This library now totals 613 million passwords and is growing.
You can bet that if you’re using plain text passwords like “Password123” or “123456” or “Qwerty1” that your password is included in this library. What this means is that, without further protection, all a hacker might need to do is find your email or username, and then run a list of passwords like this in repeated login attempts until they successfully hit on yours.
That would be a very serious problem in itself, however, if you’re using this compromised password on multiple accounts, not only does the hacker have access to the account they originally broke into, but all of those additional profiles too.
This is where password managers come in useful. A password manager can keep track of multiple different passwords across different sites. They can autofill your information for you and protect all your logins under a single master password that you set. Some password managers and even some browsers will even help auto-generate secure passwords for you. This is a brilliant way to generate a strong password immediately that you can then store safely within your password manager.
When creating a password to protect your password manager, it naturally needs to be as strong as possible. This means that it needs to be at least 12 characters long and contain letters, numbers and symbols. Additionally, it shouldn’t contain any words that mean something personal to you or relate to a part of your life. For example, you shouldn’t include the name of your partner or your first car as cybercriminals sometimes use these pieces of information to narrow down their search for your password.
Struggling to come up with a strong password that’s memorable? Here’s a nifty trick to get you started:
Think of a phrase, at least 12 words in length
“I really fancy eating a slice of pizza outdoors in the sun”
Take the first letter of each word
“irfeasopoits”
Capitalise three letters
“irFeAsopoiTs”
Switch two letters to numbers
“1rFeAs0poiTs”
Switch two letters to symbols
“1rFeA$0po/Ts”
This will help you to create a much stronger password that is much less likely to be compromised. So in order to make sure all your passwords and profiles are secure, these are the steps we would recommend.
-
Check your master password against haveibeenpwned.com’s records to make sure it hasn’t been compromised.
-
Set up a password manager to store all your login details
-
Generate new logins for each of your profiles if you're using the same details in different places
-
Make sure your master password is as secure as possible and use this for your password manager.
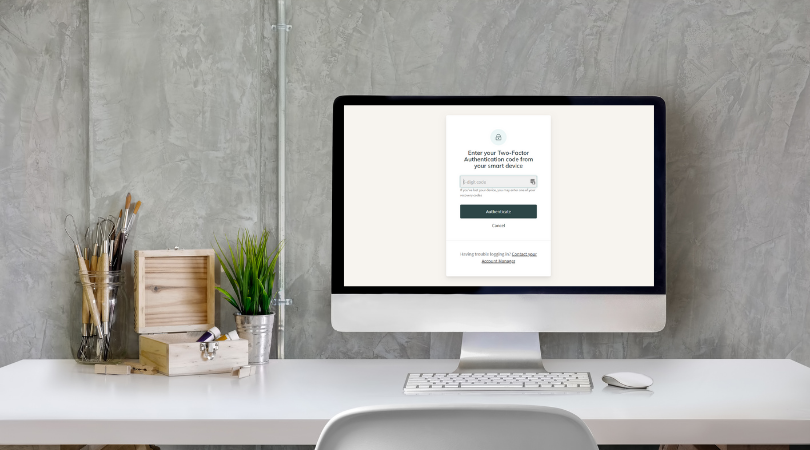
Layer Up Your Security with Two-Factor Authentication
Setting up a password manager and using only strong passwords for all your logins is an important step in securing your profiles. However, there are still ways for a cunning cybercriminal to work their way through this one layer of login security. To properly protect your profiles in the most secure way possible, you should be using two-factor authentication (2FA).
Even if someone were able to get past your username and password login, 2FA offers an extra layer of security that requires access to a separate device to the one attempting to be logged in on. This makes it incredibly difficult for anyone other than yourself to log in to your account.
If you’re on Create, our 2FA utilises authentication apps that will provide you with a unique code that you can use to sign in. Getting 2FA set up is straightforward and only takes a few minutes. We'd strongly recommend taking a moment to enable this on your account (and for any other services you use where 2FA is offered) to add an extra layer of security to your website that protects the data of you and your customers.
Don’t Share Your Login Details
At times, you will need to share access to some of your profiles. Where possible, you should always provide people with the means to create their own separate login to access any software or sites you use.
This ensures that:
-
Any activity conducted under separate logins can be monitored.
-
Any sensitive data is protected under your own login details.
-
They can’t change your password and take control of your accounts.
-
You will be compliant with GDPR and PCI DSS recommendations.
When it comes to protecting the business data your profiles hold, you can never be too careful. Even when passing your login information to people you trust, like friends and family, you can’t account for their setup or security on their device. It’s always safest to make sure you can provide them with their own means of logging in securely.
If you use Create, our Website Administrators Feature is a great example of how you can work with someone without compromising your own login details. You are able to invite admins to create their own login details, delegate site responsibilities and block access to certain pages and data. This keeps you compliant with the data protection standards and keeps everyone’s information safe.
Know How to Spot Phishing Attempts
Phishing emails are rife and unfortunately, part and parcel of being online. Everyone receives them and for the most part, they’re easily identified by numerous spelling errors and absurd requests. However, they are only becoming more and more elaborate and harder to identify, so it’s a good idea to know what some of the telltale signs of phishing emails are.
What are phishing emails? They can come in lots of different forms and can be utilised to infect malware on a recipient's device, or to collect data that would allow a cybercriminal to impersonate you to their own ends. In many cases, the emails will look like they’re sent from a well-established business. They often ask for you to confirm your details or click a link to confirm some information. They can look very legitimate, but there are some things you can do to check an emails authenticity:
-
Check their email address - Look out for letters that have been changed for numbers, and randomly generated sequences of letters, numbers and symbols. For example, if an email includes PayPal's logo but their email is something like zXY24@paypa1.com, you can assume something is off.
-
Look out for misspellings - In a lot of cases, these emails are riddled with misspellings. A reputable company simply would not stake their reputation on bad spelling and grammar. This is one of the most common indicators of a phishing email.
-
Contact the company by phone - They will be able to confirm with you whether they have sent you any emails recently and if the email is phishing or not.
By no means should you click any links in an email you are unsure of. This is another way that your computer could be infected with malware.
If you find yourself on a new website that you are unsure of, there are a few more indicators you can check for to determine if someone is phishing for your details:
-
Check that the URL is what you would expect - Like in the emails, if the URL for what you expect to be amazon.com turns out to be amaz0n.com, you are on a phishing website.
-
Check to see if they have SSL Encryption - Your browser will flag unsecure websites to you, but you can double-check by looking at the start of the website’s URL. Check for a padlock icon and see if the URL starts with https:// as opposed to http://
-
Don’t trust any pop-ups asking for information - Pop-ups will occur on most websites you visit online. It is better to search for a secure page with terms and conditions than to enter any information into a pop-up.
-
Use an anti-phishing browser or install a plug-in - All the reputable browsers will have options available to protect you from suspicious websites.
Every business will come across a phishing threat at some point. That’s why it’s important to be vigilant and have a procedure in place in case of attack. Following the points above and making sure the people you work with know how to detect a phishing attempt will help to keep your sensitive data safe.
Secure Your Website with SSL Encryption
Where you enter a website’s URL, do you see the padlock icon? That means the website has SSL encryption enabled. If it’s not there, it usually flags to you that the page you are on is not secure either in grey or red with a warning sign. You should always check for the padlock icon before you enter usernames or passwords into a website and when you’re completing a purchase online.
SSL stands for “Secure Socket Layer” and keeps the connection between someone looking at your website and the server delivering your website private so that information exchanges can’t be intercepted. Think of it in terms of having a conversation. If you have a conversation out in the open, anyone can listen in and use what you’re saying. If you take your conversation into a private room and lock the door nobody can “overhear” what is said. It’s completely private. This is why it is so important to have SSL encryption through a checkout process. You don’t want someone sitting between you and your customer in the middle of a transaction, gathering all the data!
SSL encryption has become an important trust factor to online shoppers, and is a key indicator that a website is reputable and safe. Your customers have come to expect this and will be actively looking to see if you have taken the steps necessary to make sure their data is protected.
If you're using Create, you don't need to worry about having SSL enabled. We take care of everything for you and your site will automatically have this encryption set up.
Wrapping Up
Being online comes with risks of cyber threats against your business. Hopefully, you’ll never need to encounter one. However, at the same time, it falls to you to make sure that you have every precaution in place to protect both your own personal data and that of your customers.
The tips in this article, when combined together, form a strong defence against would-be attackers. These cybercriminals are looking for easy wins from both small and big businesses alike. If you’ve taken these actions and applied them to your website and associated accounts, these defence mechanisms will help to ward off threats.
If you’re looking for a website builder that helps you to implement features such as two-factor authentication, website administrators and SSL certificates, Create has everything available to help you keep your website data secure. Start your free trial and see how else we can help you to take your online presence further.
Want Your Own Website?